
This treemap was generated with the Treemap 4.1 tool from University of Maryland. This is a tutorial that I wrote on how to get to the output, step by step.
As I just commited an option for the Picviz pngcairo plugin to draw curves instead of straight lines.
To me it just looks pretty without anything technically interesting behind it. I guess some people could argue this helps uncovering clusters, maybe... What do you guys think of such ways of playing with parallel coordinates?
The 6th International Workshop on Visualization for Cyber Security (VizSec) will be held October 11, 2009 in Atlantic City, NJ, USA in conjunction with VisWeek 2009.
The deadline for full papers (12 pages) is May 8, 2009. The deadline for short papers (6 pages) is May 22, 2009.
Please see the web site for formatting instructions, templates and information on how to submit your paper.
Best,
-john
Take a look at my site www.manntechcomputersinc.com We have developed a visualization tool for pix/asa and snort. It maps ip to geographical locations countries (source or destination), anonymous proxies , sat providers, regions etc. We repsent countries by flags and provide users to add their own icons. I'd be interested to hear what people think....
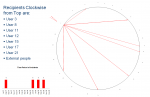
see http://5thsentinel.wordpress.com/2009/04/01/inappropriate-content-visualization/ for background.
This is similar to the Visio diagram that showed all the inappropriate email attachments that a specific user sent. However a time line was included to better articulate number and time of incidents.
The chart represent several hours of conficker's P2P Udp activity, it relates destination address with dest UDP used.
This is my smart analysis about the first 20days of April 2009 ccTLD (country code top level domain) generated by the algorithm used by worm for pseudo random domain name generation.
The following chart show the frequency for each ccTLD. As you can see there is a sort of attractor for some ccTLD such as AG, BO, LC, HN, PE, and TW. A singular point is for DJ ccTLD domain. For more information http://extraexploit.blogspot.com. This kind of analysis I think that is usefull for get evidence as indicator of conficker.c activities inside your corporate network.
Feedback are well come.
Regards
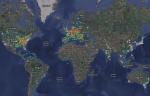
This was made using gheat to generate a nice map of locations that are attacking our SensorNET.
SensorNET is a set of distributed nepenthes sensors that we set up at the Australian Honeynet Project.
Scans from attacking IP's and network borne malware is captured and analyzed.
These attacks are portrayed on this heatmap.
For full story go here http://honeynet.org.au/?q=node/41
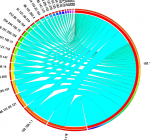
I'm working on a project which aims to visualize relations between IP with different ways. So, I'm opened for all ideas !
This graph was created with Circos. I use some Python scripts to get the IPs and generate the Circos matrix.

R Project is an open-source software for statistical computing. It is a very comprehensive suite and offers many 2D and 3D visualizations. Data can easily be imported from file or even database.
The histogram shows the distribution of the scanned TCP ports when using nmap in default mode against one target system. The other plot shows the order of the TCP ports being scanned. We can see that the ports are scanned rather randomly and not in sequence as one might expect. The data for the visualization was extracted using tshark, the command line version of Wireshark.
The plots where generated with following commands:
root@davix:~/# tshark -r nmap_option_v_oA.cap -Tfields -Eseparator=, -R "ip.dst == 192.168.119.135 and tcp" -e tcp.dstport | sort -n | uniq > tcp_ports_sorted.csv
root@davix:~/# tshark -r nmap_option_v_oA.cap -Tfields -Eseparator=, -R "ip.dst == 192.168.119.135 and tcp" -e tcp.dstport > tcp_ports_unsorted.csv
root@davix:~/# R
R version 2.6.1 (2007-11-26)
Copyright (C) 2007 The R Foundation for Statistical Computing
...
> results <- read.csv("tcp_ports_sorted.csv", header=T);
> attach(results);
> names(results);
> png(filename="tcp_port_histogram.png");
> hist(TCP_PORT, freq=TRUE, col="lightblue", breaks=seq(from=0, to=70000, by=1000));
> dev.off();
...
> results <- read.csv("tcp_ports_unsorted.csv", header=T);
> attach(results);
> names(results);
> png(filename="tcp_port_over_time.png");
> plot(TCP_PORT, col="blue");
> dev.off();
> q();
If you are looking for a quick and easy introduction I recommend looking at the first three chapters in Jane Horgan's book "Probability with R: An Introduction with Computer Science Applications".
This is a timeline visualization of surfing activity recovered from Internet Explorer cache index.dat files. The graph was generated with the SIMILE Timeline Widget AJAX API. The graph has two timeline bands: The bottom one gives an overview of the activity over the complete timeline and the top one shows the details. The graph can be interactively navigated by panning the graph right/left. Different magnification levels can be set for each timeline band and also within a timeline.
Extraction from the index.dat files was done with Pasco. With awk/sed and some manual tweaking the data was transformed to a XML that can then be visualized with the API.
 SecViz has a mailinglist!
SecViz has a mailinglist!
The charter for the list is the same as for the SecViz Web site: share, discuss, challenge, and learn about security visualization. The mailinglist should help to have more in-depth discussions and get quicker responses on specific topics. I am looking forward to some good discussions around visualization applications, visualization methods, use-cases, etc. Fire away!
Note that the list keeps a public archive!

This image is a screenshot of nf3d. This software uses a GANTT like approach to display IP connections as seen by Netfilter. Connections are sorted following their start date and they are drawn from back to front under the form of a cylinder. The small balls are specific packets which are put on the the connection they belong to. Here, the balls represent SYN or FIN packets.
This image displays a ssh scan attack that can be compared with regular traffic displayed at the front (right) of the image.
VizSec 2009
Workshop on Visualization for Cyber Security
October 11, 2009 / Atlantic City, NJ USA
http://vizsec.org/vizsec2009/
The 6th International Workshop on Visualization for Cyber Security is a forum that brings together researchers and practitioners in information visualization and security to address the specific needs of the cyber security community through new and insightful visualization techniques. Co-located this year with IEEE InfoVis/Vis/VAST, VizSec will continue to provide opportunities for the two communities to collaborate and share insights into providing solutions for security needs through visualization approaches. Accepted papers will be published by the IEEE and archived in the IEEE Digital Library. The authors of the best papers will be invited to extend and revise their paper for journal publication in a special issue of Information Visualization.
This year our focus is on advancing Visualization for Cyber Security as a scientific discipline. While art, engineering, and intuitions regarding the human element will always remain important if we are to obtain useful cyber security visualizations, advances in the scientific practice of research are needed. The scientific aspects of visualization for cyber security draw both on empirical observation (similar to many natural and social sciences) and formal science (such as the formal derivations in mathematics). Barriers confronting current researchers include concerns about available data, lack of a common agreement about what constitutes sound experimental design, the difficulties of measuring the relative effectiveness of security visualizations in practice, and the lack of a common understanding of user requirements. While many researchers are making progress in these and other critical areas, much work yet remains.
What To Submit
Papers offering novel contributions in security visualization are solicited. Papers may present technique, applications, practical experience, theory, or experiments and evaluations. Papers are encouraged on technologies and methods that have been demonstrated to be useful for improving information systems security and that address lessons from actual application. We encourage papers that report results on visualization techniques and systems in solving all aspects of cyber security problems, including how visualization applies to:
*Different aspects of security: software, networks and log files (e.g., Internet routing, packet traces and network flows, intrusion detection alerts, attack graphs, application security, etc.)
*Application of visualization techniques in formalizing, defining and analyzing security policies
*Forensic analysis, correlating events, cyber-defense task analysis
*Computer network defense training and offensive information operations
*Building rules, feature selection, and detecting anomalous activity
*Software, software security, and viruses
*Deployment and field testing of VizSec systems
*Evaluation and user testing of VizSec systems
*User and design requirements for VizSec systems
*Lessons learned from development and deployment of VizSec systems
*“Field Research” Best Practices
*Interaction with domain experts – best practices, lessons learned
*Differentiating the needs of different domains and time frames
*Best practices for obtaining and sharing potentially sensitive data for purposes of visualization and assessment, including how to approach personal privacy, regulatory, and organizational issues
*Metrics and measurements (e.g., criteria for the relative effectiveness of cyber visualizations)
*Handling large datasets, scalability issues, and providing real time or near-real time visualizations
Accepted papers will be published by the IEEE and made available through the IEEE Digital Library.
Paper Format:
Submitted papers must not substantially overlap papers that have been published or that are simultaneously submitted to a journal or a conference with proceedings. All submissions should be appropriately anonymized (i.e., papers should not contain author names or affiliations, or obvious citations). Submissions are to be made to the submission web site at http://www.vizsec.org/vizsec2009/submit. Only pdf files will be accepted. Papers should be formatted using the IEEE templates (see http://www.vizsec.org/vizsec2009/ for instructions).
*Full papers should be at most 12 pages, including the bibliography and appendices.
*Short papers should be at most 6 pages, including the bibliography and appendices.
Committee members are not required to read the appendices, and so the paper should be intelligible without them. Submissions not meeting these guidelines risk rejection without consideration of their merits. Authors of accepted papers must guarantee that their papers will be presented at the conference.
Papers must be received by the deadline of April 24, 2009, for long papers and May 22, 2009, for short papers.
Journal Special Issue
The authors of the best papers from the accepted program will be invited to extend and revise their paper for a special issue of Information Visualization (IVS), an international, peer-reviewed journal publishing articles on fundamental research and applications of information visualization. These papers will be chosen by the program committee.
Paper Award
There will be an award for the best paper from the accepted program. The best paper award will be given to the paper judged to have the highest overall quality. A key element of the best paper selection process will be whether the results are believed to be repeatable by other scientists based on the algorithms and data provided in the paper. This award will be chosen by the program committee.
Scholarships
A limited number of scholarships will be available for students and first-year faculty who have had papers accepted to VizSec.
Organizing Committee
General Chair Deborah Frincke, Pacific Northwest National Laboratory and University of Washington
Program Co-Chair: Carrie Gates, CA Labs
Program Co-Chair: John Goodall, Secure Decisions Division of Applied Visions
Papers Chair: Robert Erbacher, Utah State University
Program Committee
Richard Beijtich, General Electric, USA
Greg Conti, United States Military Academy, USA
Marc Dacier, Symantec Research Labs, France
Anita D’Amico, Secure Decisions div. of Applied Visions, USA
Ron Dilley, Information Security Professional, USA
Dave Ebert, Purdue University, USA
Glenn Fink, Pacific Northwest National Lab, USA
John Gerth, Stanford University, USA
Warren Harrop, Swinburne Univ. of Technology, Australia
Mark Haselkorn, University of Washington, USA
Richard Johnson, Microsoft, USA
Richard Kemmerer, UC Santa Barbara, USA
Toby Kohlenberg, Intel, USA
Florian Mansmann, University of Konstanz, Germany
Raffael Marty, Splunk, USA
Doug Maughan, Department of Homeland Security, USA
John McHugh, Dalhousie Univ., Canada, and Univ. NC, USA
Jan P. Monsch, Dublin City University, Ireland
Chris North, Virginia Tech, USA
Stephen North, AT&T Research, USA
Sean Peisert, UC Davis, USA
Greg Schmidt, SPADAC, USA
George Tadda, Air Force Research Lab, USA
Ed Talbot, Sandia National Laboratories, USA
Joanne Treurniet, Defence R&D Canada, Canada
Grant Vandenberghe, Defence R&D Canada, Canada
Kirsten Whitley, Department of Defense, USA
Pak Chung Wong, Pacific Northwest National Lab, USA
Tamara Yu, Massachusetts Institute of Technology, USA
http://vizsec.org/vizsec2009/