In conjunction with the 2013 IEEE International Conferences on Intelligence and Security Informatics (ISI), we present a special topics workshop on:
Evaluating Security Visualizations in Supporting Analytical Reasoning & Decision Making in Cybersecurity
Workshop Description
As the potential for visualizations in cybersecurity analysis becomes exceedingly more apparent, efforts to evaluate these visualizations become more imperative than ever to supporting the cybersecurity mission. As technology and big data continue to grow rampantly so does the deployment of insufficiently evaluated cybersecurity visualizations that claim to be most aligned with how analysts think and perceive data. Before organizations may intelligently incorporate visualization into their cybersecurity analysis process they must be prepared to pose tailored sets of questions that directly relate to the particular objective of the cyber analyst. This workshop addresses these gaps with the intent of bringing together experts from a variety of disciplines relevant to the topic of evaluating cybersecurity visualizations in their ability to support analytic reasoning and decision making in cybersecurity.
Paper Topics
We welcome paper submissions on the following or related topics:
Empowering the Human Analysts
Methods and techniques for evaluating the impact cybersecurity visualizations have on enabling the human perception and cognitive processes that are required for intelligent decision making.
Addressing current deficiencies in cybersecurity analysis
Methods and techniques for measuring the impact cybersecurity visualization tools have on addressing current deficiencies that still exist in cybersecurity analysis such as exploration and prediction.
The Unique nature of Cybersecurity Visualization
Identifying aspects that are specific to cybersecurity visualization, and identifying relevant contributions from current research in the broader fields of information visualization and scientific visualization, and from visualizations in other domains.
Important Dates
Workshop papers due: March 31, 2013
Notices of acceptance and comments provided to authors: April 12, 2013
Camera ready paper submitted: April 29, 2013
Website: http://www.isiconference2013.org/pgs/workshop-on-cybersecurity-visualizations.php
Paper Submission:
Submission file formats are PDF and Microsoft Word. Required Word/LaTex templates (IEEE two-column format) can be found on IEEE's Publications web pages. Submissions can be long (6,000 words, 6 pages max) or short (3000 words, 3 pages max). Papers in English must be submitted by email to Lisa Coote at Lisa.Coote@innovative-analytics.com. The accepted workshop papers from will be published by the IEEE Press in formal Proceedings. Authors who wish to present a poster and/or demo may submit a 1-page extended abstract, which, if selected, will appear in the conference proceedings.
Conference content will be submitted for inclusion into IEEE Xplore as well as other Abstracting and Indexing (A&I) databases. The selected IEEE ISI 2013 best papers will be invited for contribution to the Springer Security Informatics Journal.
Organizing Committee:
Kevin O'Connell, Innovative Analytics & Training
Lisa Coote, Innovative Analytics & Training
Program Committee:
Raffael Marty, PixlCloud
Tomas Budavari, John Hopkins University
Antonio Sanfilippo, Pacific Northwest National Laboratory
John T. Langton, VisiTrend LLC
Claudio Silva, NYU Polytechnic
Bernice Rogowitz, Visual Perspectives Consulting
Cullen Jackson, APTIMA
Enrico Bertini, NYU Polytechnic
John Goodall, Oak Ridge National Laboratory






.jpg)


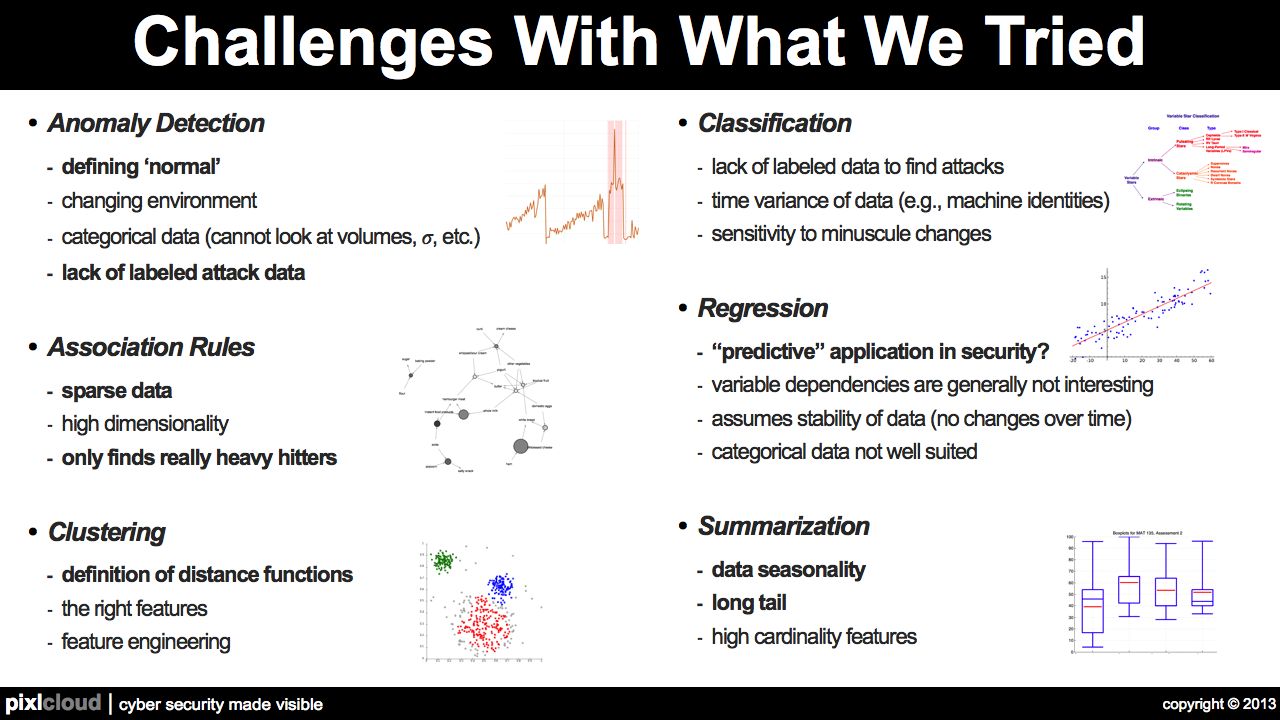
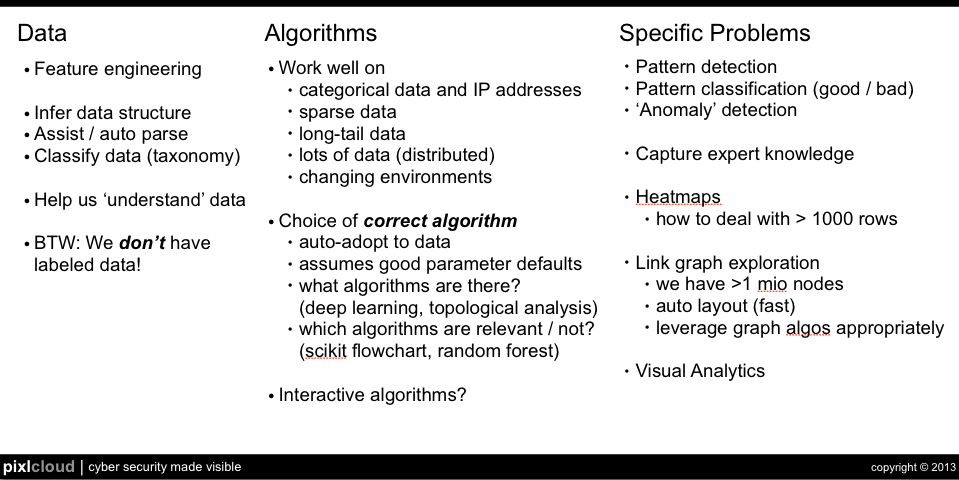

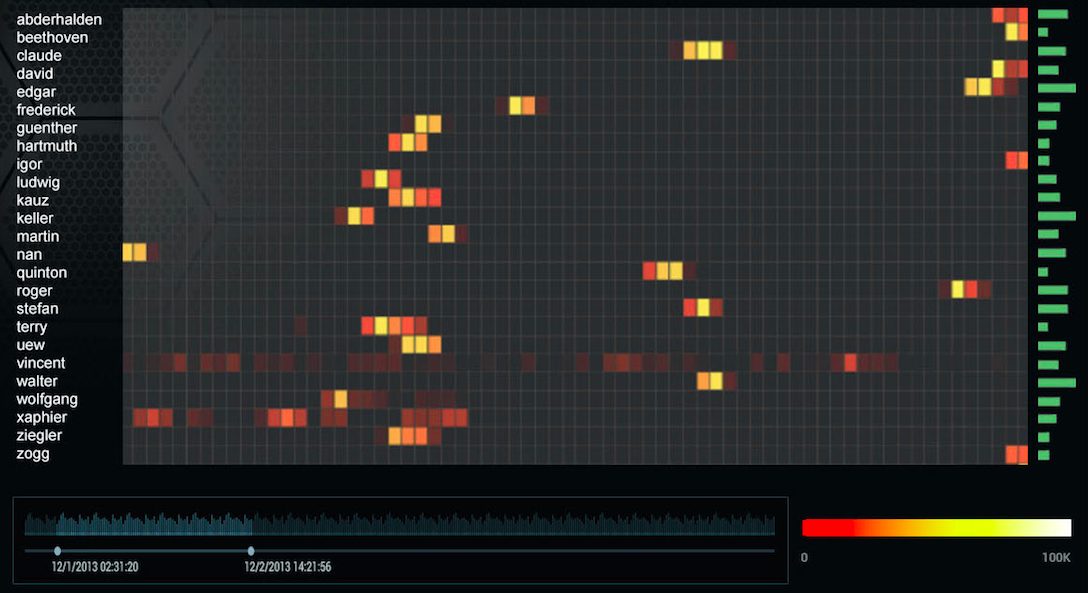
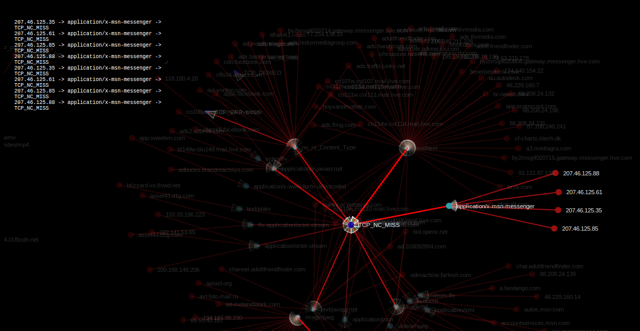
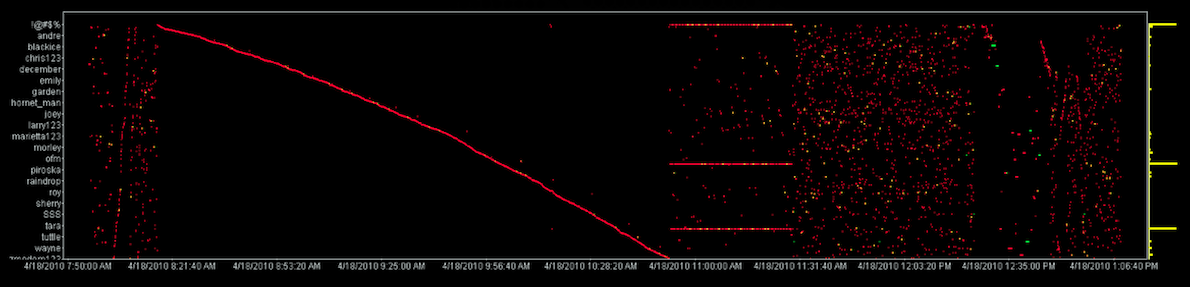
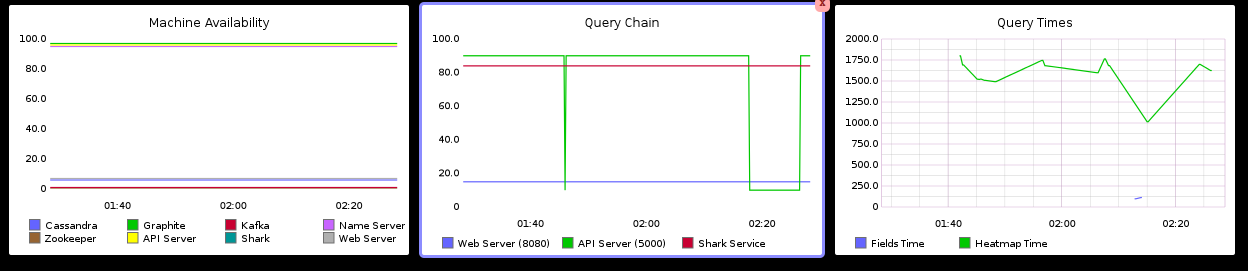
 In December I'll be presenting on security intelligence and the interplay of visualization and data mining.
In December I'll be presenting on security intelligence and the interplay of visualization and data mining.